TryHackMe: Avengers Blog
We Have A Hulk
'Learn to hack into Tony Stark's machine! You will enumerate the machine, bypass a login portal via SQL injection and gain root access by command injection.'
Hello all! I'm Jin, and welcome to my blog. Today's write-up is on the THM Avengers Blog room which I completed as part of the Web Vulnerabilities course on TryHackMe. I'll admit I blazed through this course because a lot of it was things I had previous experience with thanks to PentesterLab. If you're looking for ways to supplement your learning, I definitely recommend it.
Anyhow, this is a sweet and simple box with a good walkthrough in the tasks themselves so we'll mostly just be documenting process here. That said, let's go~
Task 2 - Cookies
Task 1 just has us connect to the machine, so we'll start with task 2.
Task 2 is cookies. Cookies can do a lot of things, like store login info, shopping cart items, basically anything the website needs to remember about you and your session since that information isn't stored on the website itself. Cookies can also be used to track traffic and some anti-virus classify them as spyware.
Question 1: On the deployed Avengers machine you recently deployed, get the flag1 cookie value.
To view cookies, we can hit F12 to bring up the console and click Storage (on Firefox).
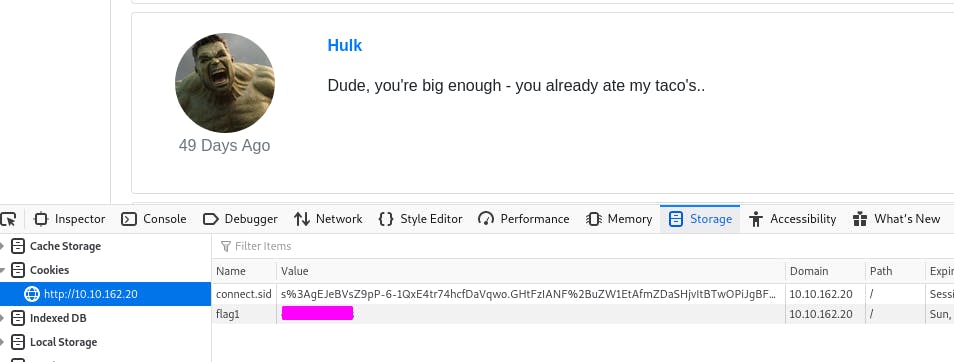
And right away we see our flag.
Task 3 - HTTP Headers
HTTP headers let a client and server pass information with an HTTP request or response. Header names and values are separated by a single colon. The main two HTTP methods are GET and POST. GET requests data from a resource and POST sends data to a server.
Question 1: Look at the HTTP response headers and obtain flag 2.
Back to the Developer Tools, this time the Network tab. We may need to hit refresh (F5) to have the requests logged here.
Clicking on a request displays its data on the right, and right away we spy our flag.
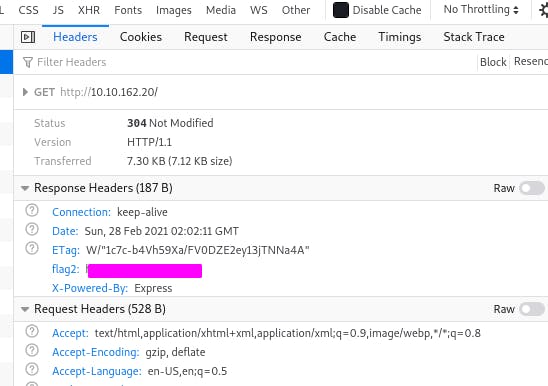
Note: Intercepting requests with Burp or Zap is a great way to view (and edit!) headers.
Task 4 - Enumeration and FTP
Next up we'll be scanning the machine with nmap. If this isn't your first time with me, you're probably familiar with my preferred scan nmap -A -p- [ip] -vv. For this machine, however, we'll follow the instruction.
Let's scan with nmap 10.10.162.20 -v as instructed.
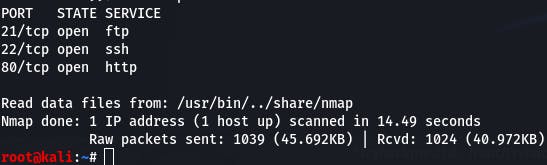
Our scan tells us that there's FTP and SSH on this server. Let's try FTP with the credentials we found.
What credentials? Well...
groot:iamgroot seems likely. Let's try it.
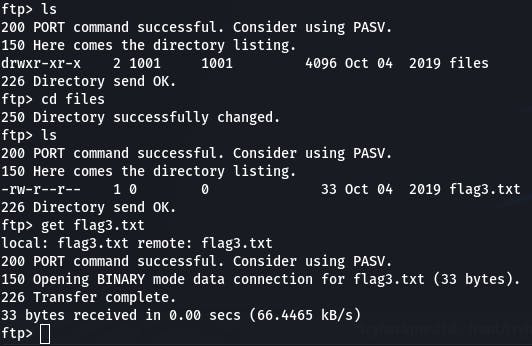
Question 1: Look around the FTP share and read flag 3!
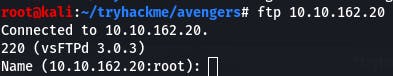
First, we connect to FTP with ftp 10.10.162.20.
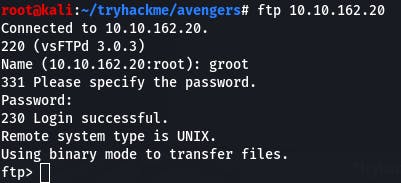
Then we enter the credentials we found.
We can use use basic Linux to navigate the share, and get to download the flag.
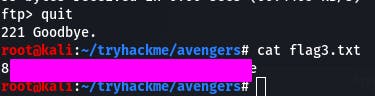
Then we can cat the flag on our local system.
Task 5 - GoBuster
GoBuster can help us find directories that aren't readily available by just clicking around. It brute-forces URIs (directories and files, DNS subdomains, and vhost name. Here, we want to see if there are any hidden directories to explore.
Question 1: What is the directory that has an Avenger's login?
We'll use the command gobuster dir -u http://10.10.162.20 -w /usr/share/wordlists/dirb/common.txt to see what we can see.
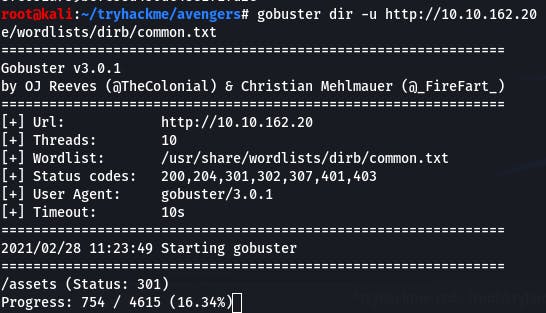
Assets popped up!
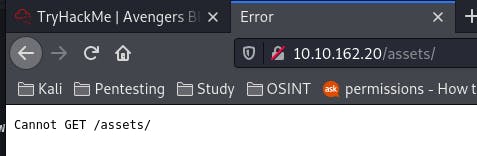
But navigating there nets us nothing. It's still worth trying though, because more access is always better than less (for us).
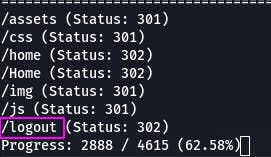
In the spirit of trying things, /logout popped up so we try it. Not blindly though, because its marked as 302 -- redirect. And where do logouts usually redirect to?
That's right, login portals. GoBuster also confirms our suspicions.
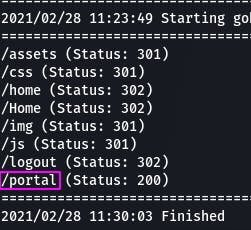
The lesson here? Tools are great, but you don't have to rely wholly on them when you've got a perfectly good head on your shoulders. Use it~
Task 6 - SQL Injection
On to SQL Injection, or SQLi for task 6.
SQLi relies on knowing how SQL works, which is explained in the task. Basically, we want the expression we're sending data to to evaluate as “True” without comparing to any data stored elsewhere. 1=1 is always true, so that becomes integral to our payload.
Question 1: Log into the Avengers site. View the page source, how many lines of code are there?
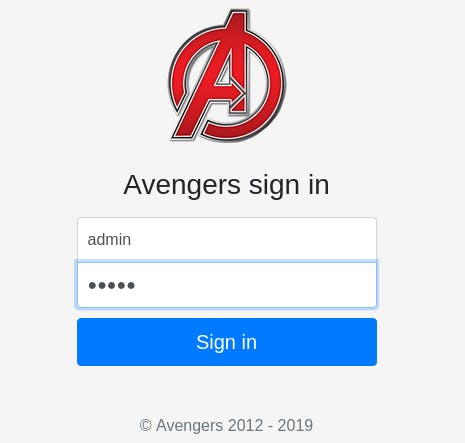
Just to be safe, we test admin:admin. It's tradition, after all.
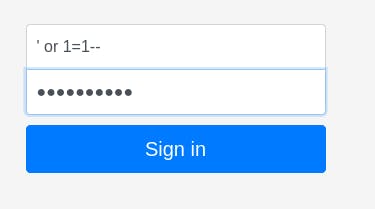
For the actual SQLi, we use the “credentials” ' or 1=1--:' or 1=1--.
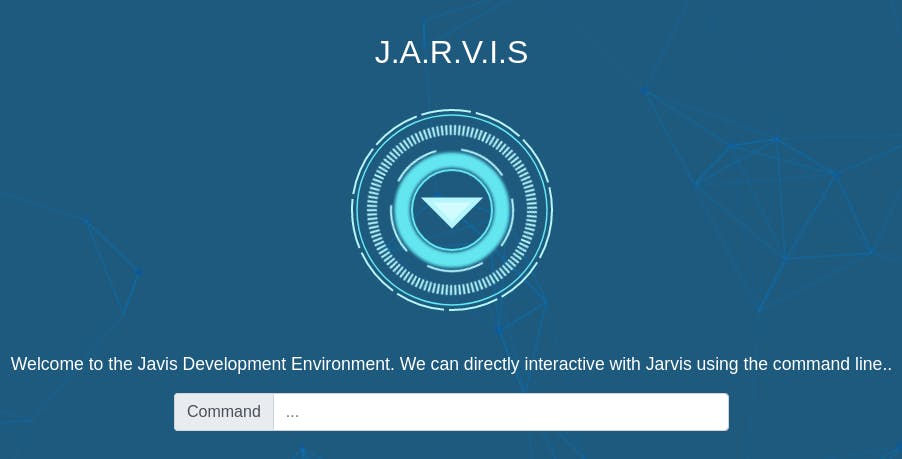
And we're in! Now we need to find out how many lines of code are in the page source.
We can do that by right-clicking the page and left-clicking View Page Source from the pop up menu.
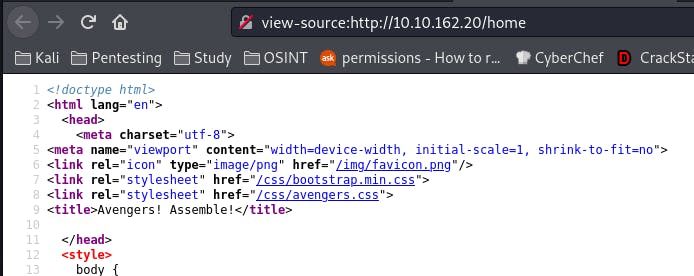
(Navigating to view-source:[url] will also do the trick.)
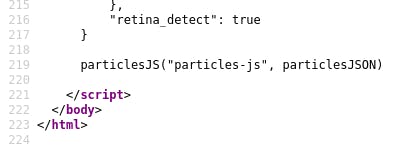
Scrolling to the bottom shows us we have 223 lines of code.
Task 7 - Remote Code Execution and Linux
Once logged in, we have a control panel! Following the instruction provided shows us the location of the flag, but we can't use cat. (I also learned about chaining commands with ‘;’)
Question 1: Read the contents of flag5.txt
If we can't use cat, how do we read files? I can think of a couple ways.
First, tac. It's cat, but reads files backwards line by line.
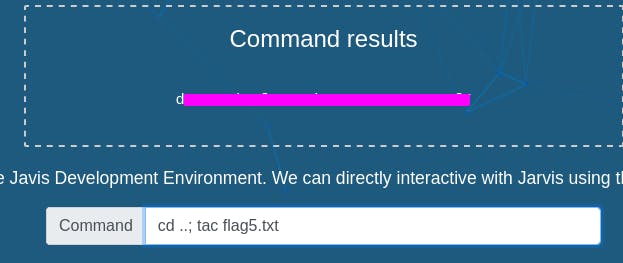
we can also grep the file in question, searching for an empty string. Nothing matches everything, so we get everything back.
grep ‘’ flag5.txt
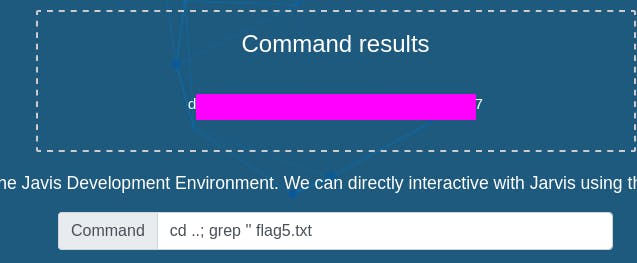
The grep method is useful if we want to retain the file's order.
With that flag, the Avengers room is complete~
Endgame
So that was the Avengers Blog! How was it? After coming this far with the beginner's path and now here at the end of the web vulns path, I'm really feeling good about the basics. Of course, this is a field that's always changing, growing, rapidly shifting and expanding, but like anything else, it's solid fundamentals that growth and progress are built on. Instead of looking at unknown machines with worry if I'm good enough, I'm now starting to relish the chance to get stuck and learn something new. It's a wide world out there, so hack safely, and build that confidence to not only take you where you want to go, but figure out a way when none seem apparent.
That's all for now. Thank you for reading, and see you in the next bit~